Watch Trava’s CEO, Jim Goldman, present an integrated approach to cyber risk management at the January 12, 2021, meeting of the Ohio River Valley chapter of the Cloud Security Alliance.
About Cloud Security Alliance:
The Cloud Security Alliance (CSA) is the world’s leading organization dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment. CSA harnesses the subject matter expertise of industry practitioners, associations, governments, and its corporate and individual members to offer cloud security-specific research, education, certification, events, and products. CSA’s activities, knowledge, and extensive network benefit the entire community impacted by cloud—from providers and customers, to governments, entrepreneurs, and the assurance industry—and provide a forum through which diverse parties can work together to create and maintain a trusted cloud ecosystem.
Transcript:
Greg Allender (co-host): And so let’s get started. Our first presentation, we have Jim Goldman, CEO and co-founder of Trava. And so Jim is the CEO, co-founder of Trava Security, which simplifies holistic cyber risk management with automated vulnerability assessments, mitigation recommendations, and cyber insurance.
Greg (continued): Jim has over 30 years experience in cybersecurity and risk management. He served as professor and head of the Purdue Malware Lab and Department of Information Technology at Purdue University, where he founded the network engineering technology program. He was the first VP of information security at ExactTarget, which was later acquired by Salesforce. And at Salesforce, Jim held various executive positions, culminating in his assignment to build the global security governance, risk management, and compliance team for all of Salesforce.
Greg (continued): Jim is a CISSP with advanced training in cyber forensics and malware reverse engineering. He served as a task force officer detailed to the FBI cyber crime task force, serving on both the national security and criminal cyber squads. And he’s an internationally published author with market-leading textbooks in data communications and networking and frequently invited conference speaker. So with that, I’ll turn it over to you, Jim.
Jim Goldman: Thank you, Greg. Okay, do I have control of the slides, or do I need to share my screen?
Shawn Altman (co-host): You want to share, if not I can give you, I can also—
Jim: I’m ready to share, thank you.
Shawn: Yep, and while he’s getting that ready, guys, feel free to ask questions as we’re going along using the chat, and then when we get towards the end of each presentation you can unmute and also ask questions live.
Greg: Okay, so just, Jim, sorry, just a reminder as well. We are recording this presentation today, so we will make it available on our website, but just want to make sure everybody understands that we’re recording as well. So go ahead, Jim, thanks.
Jim: You bet, so can everybody see my screen?
Greg and Shawn: Yes, it looks good. Yep.
Jim: Okay, great, so I appreciate the outline because I, you know what’s interesting, when we started Trava, we actually took the same approach. We recognized the problem, and then we stepped back and said, “Okay, how do we approach the problem, how’s that turn into a viable business or a product, and then how do we get that to market?” And so this outline is actually, in some ways, a history of what we went through to develop Trava.
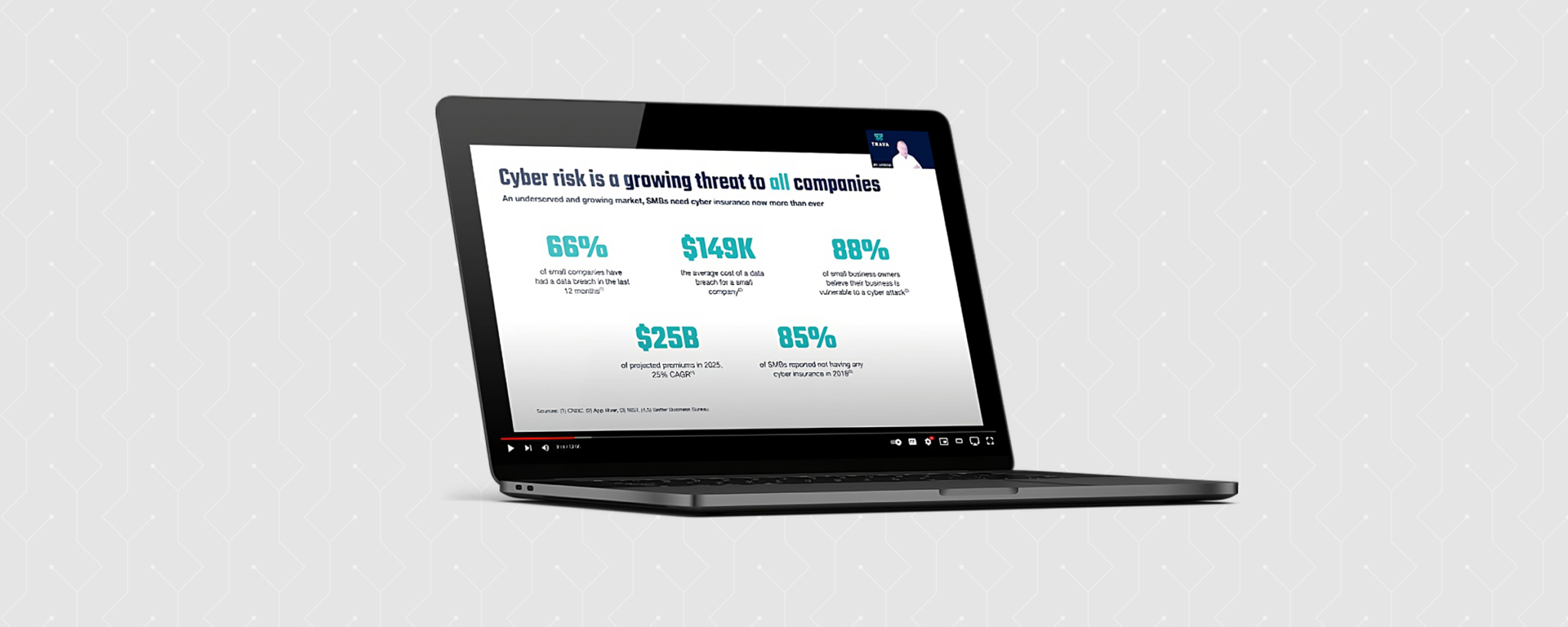
Jim (continued): So let’s start with the problem, and some of you may be familiar with some or all of these statistics, but I think they are worth repeating or bringing up again, at least some of them. And they come from a variety of sources, and I’ve cited those sources below. It’s estimated that two out of every three small companies have had a data breach in the last 12 months. I think the estimate of the average cost of the data breach for a small company may be a little bit low, especially when ransomware is involved. Most owners of small businesses believe they have a problem, believe they are vulnerable to a cyber attack, and yet about the same percentage—85 percent—have no cyber insurance whatsoever.
Jim (continued): Meanwhile, the cyber insurance industry is expected to grow significantly in the next five years. An underlying statistic that’s not on this sheet, that I believe is very relevant to the importance of this issue and this market, that many of you may be familiar with is that two out of every three new jobs in the United States is created from small business. And so you have an incredibly important segment of the United States economy that’s being forced into digital transformation like never before, accelerated by the pandemic. And yet, as ill equipped as they are to go to digital transformation, they’re even more ill equipped to protect those businesses, protect those online assets.
Jim (continued): So that, in a nutshell, is the environment. It’s not the essence of the problem, it’s not the real point to the spear, as they say, of the problem, but it’s the overall environment that we walked into. And so what, let’s look at the problem a little more deeply. Why can’t this problem, why hasn’t this problem been addressed more effectively in the past? And it’s really because, in the United States at least, that this is traditionally addressed by two very different industries. On the one hand, you have the cyber risk management industry, cybersecurity industry, of which many of us are a part. On the other hand, you have the cyber risk transfer part of cyber risk management, with cyber insurance that’s done by the insurance industry, which as we know is, you know, highly regulated et cetera.
Jim (continued): It’s just a very different way of doing business. And so why does this matter? You know, what happens right now, the small and medium-sized businesses, is they find it very frustrating to try to bridge this chasm, to try to bring these two elements of the solution together. And we’re really leaving it in their lap, where it’s small business’s problem to bring these two pieces together, to bring the cyber insurance and the cyber risk management together, and as a result they end up wasting time and wasting money. They’re not sure about the protection they get. We’ve spoken to many clients that say things like, “I absolutely love my insurance broker, but he or she knows absolutely nothing about cyber insurance.”
Jim (continued): And so here was our approach. Conceptually, we said, “What if we were to build a bridge between the cyber risk management part of the business and the cyber insurance part?” And that bridge is kind of both literally and figuratively, in the sense that we’re building a data bridge. Our cyber loss data prediction platform gathers data from both sides of the bridge. One of the problems and the differences in the industry is that they don’t even speak the same language, they don’t use the same data constructs, that type of thing. And so we’re building this data bridge between those two elements.
Jim (continued): This—the comprehensive risk management—is familiar to many of us on the call, but let me just go over this quickly to show you how this works. Obviously, you have to start with assessment, and you have to be able to identify the risks that you have and know where those shortfalls are, and note those things that need to be fixed, right, you know, vulnerability assessment, you do risk assessments, etc. And that’s what we’ve developed, as you’ll see shortly, that’s how we’ve developed our products, to make this easy for the small or medium-sized business or for the managed service provider that—I’m sorry, I’m just watching my stuff, my stopwatch there, so I don’t go over—or for the managed service provider that is serving those small and medium-sized businesses. Because what we find in this small or medium-sized business is, they generally don’t have their own IT resources, certainly not their own security resources, they depend on managed service providers to be their trusted advisors.
Jim (continued): Once the shortcomings are identified through the assessment process, the next step is to do something about them, that’s mitigation. All right, so, you know, you prioritize those things that need to be fixed, and then you have budget constraints or business priorities, you’re going to fix what you can, what you can afford to, but there are always going to be some things that fall off the bottom of the list that aren’t able to be properly mitigated right away. That’s what’s known as residual risk. What we’re supposed to do with that residual risk is be able to transfer it, and in our case, that risk transfer happens to cyber insurance as I said before.
Jim (continued): Well, conceptually, this all seems very straightforward. I don’t understand what the problem is—it should be one smooth, integrated process. In reality, it’s not that way for small and medium-sized businesses, until now.
Jim (continued): So people say to us, “So, Trava, I’m trying to understand what you do. Are you a SaaS company, or are you an insurance company?” And the answer is, “Yes.” What we do is we take an integrated approach to cyber risk management that includes assessment, mitigation, and then finally risk transfer through cyber insurance. And we offer this as a flexible offering. I mentioned before that we work through managed service providers, managed security service providers, as well as, you know, a direct sales channel. And so what we’re, what we’re showing here is that with our data platform, that we call the Trava insurance analytics platform, we can have customers using our Trava assessment tool that we’ve developed, our front-end assessment tool. Or if we’re dealing with a managed service provider or managed security service provider that’s all set in that aspect, that’s already doing their own assessments, they can still, through our API, upload their assessment data into our analytics platform, and we can still use that to help them on the mitigation stage and the risk transfer stage to cyber insurance.
Jim (continued): So let’s take a closer look at the product. What we do is, what you’re looking at here are some screenshots of our assessment product, and we not only assess, but we normalize the data across multiple scans, multiple scan types that we have integrated from multiple sources. They might be commercial scans, they might be public source, open source scans, they might be scans that we developed in house. So you have all these different flavors of scans bringing in all this data that goes into our data lake, where it’s normalized. That’s our data platform that I’ve been referring to, and then that normalized data is turned into overall scores and highlights the specific vulnerabilities by severity that need to be dealt with.
Jim (continued): Here’s some of the key product features, you know, again, we were focused on small and medium-sized businesses, so we tried to take some of the complexity out of that assessment process, out of those current assessment tools that are available on the market. As many of you know, they’re not necessarily easy to install or configure. In many cases, they don’t have very effective error handling, we’ve added that. So we built this umbrella into which we can plug and play different scans, and then we’ve added intelligence above that. We’ve added intelligence to do error handling that was not there, we’ve added intelligence to take that data out, normalize it, and then prioritize mitigations across multiple scans.
Jim (continued): We also do not just vulnerability scanning, but we do risk assessment. I know it’s a little bit hard to read, but we have a survey in our tool that basically does a shortened version of the NIST cybersecurity framework, the NIST CSF, and runs through the people, process, and technology that need to be in place in these different types of processes if you’re going to have an effective overall cyber risk management or cyber security program. So you get a maturity rating of your cyber security program with prioritized recommended courses of action in each of those areas, as well as a plan of attack down here with all your vulnerabilities listed out by severity.
Jim (continued): We do output at both the executive level and the technician level, so this is an executive-level view over here, with the overall risk ratings by scan, and then if you would drop down on any particular scan, that would go into the specific vulnerability that was found. It would talk about the source of the vulnerability, the impact of the vulnerability, and the recommended solution how to get rid of the vulnerability. It’s also very easy, again, we’ll try to make it easy for both the MSP or the small company that doesn’t have a full-time IT person or a full-time security person. They can just schedule these scans on a recurring basis. They’re not going to have to remember to go in every week or every 30 days and do these. You set them up once, they’ll run, reports come out, it’s very very easy.
Jim (continued): So that’s the assessment piece. Remember, the middle piece was mitigation. When we have direct customers, we often offer the mitigation services to them directly, and these are just a few of the virtual CISO services that we’ve offered to our direct customers. In some cases, if we’re working through our channel, working through our MSPs or our MSSPs, they already have the ability, this is their bread and butter to do the mitigation, but in some cases, we might be in the background helping them with strategic planning or doing white-label vCISO services for them. You know, this is a very cost effective way these days for small and medium-sized businesses to get the level of strategic planning they need in the security realm. Years ago, the vCISO thing wasn’t really accepted, or it wasn’t the norm, it wasn’t the mainstream. These days, I feel like it’s very much the mainstream.
Jim (continued): We’ve helped several of our customers that didn’t have a security person, you know, we deal with a lot of growing SaaS companies, they’re looking to land their first enterprise customer. That enterprise customer does a security assessment on them, comes up with multiple findings, and they’re kind of at a loss as to what to do about those. That’s where we come in. We close those findings, we put a real risk management program in place, we put a real vulnerability management program in place, they’re able to get that, you know, key business-changing, business-history-changing contract with that enterprise customer that changes the future direction of their company.
Jim (continued): And then, finally, remember the last piece. So this is the risk transfer piece, so the cyber insurance piece. We offer cyber insurance, we represent about eight different carriers right now. It’s very easy, there’s a button right in that same place where you run your assessments, there’s a button that says, “Get a quote.” You go in there, you answer some very few simple questions about your own contact information, the contact information for your business, and then there’s a business information thing with about three questions, approximate annual revenue, approximate number of records that your company holds, and the program is able to estimate it based on your revenue and the next question, which is basically your industry. It uses the industry standard classification scheme. You pick the number and the name of the industry segment that you’re in, you answer a question if you’ve ever had a previous breach or not, and then in about, within about 30 seconds, you get up to eight quotes from eight different carriers. We are a licensed insurance agency with cyber insurance specialists that then deliver those quotes. You walk through them and, you know, based on your particular situation, can help you choose the cyber insurance policy that’s most appropriate for you.
Jim (continued): This is the sales pitch. I won’t read it to you, but basically what we’re trying to do is, again, have that comprehensive cyber risk management platform, the one-stop shop, if you will, where small and medium-sized businesses can just go one place, understand what their issues are, get those issues fixed, and then have cyber insurance to, you know, have that safety net underneath them should catastrophe strike.
Jim (continued): I don’t know if we have time for a demo, we want to leave time for questions and answers. And there’s a free trial for everybody. You can just go to that link directly, or if you go to www.travasecurity.com, as you can see right there, that link right up in the top, there’s a “try free.” It is fully enabled, every feature is available. The only limitation is you can do any scan you want one time, but it’s fully featured free trial. That’s it. How’s that for time, okay?
Shawn: Oh, that’s good. So I guess, one of the questions I know you kind of talked on as you were going through, but can you talk a little bit more about how your co– how your products can work with other vulnerability scanning tools, or is there any sort of connections or integrations from that perspective?
Jim: Sure, so I would answer that question on two different levels, okay? One is we can take existing commercial or open-source vulnerability scanning tools and run them under our execution and scoring and data platform environment, so there’s no limitation as to what scans we can add. Case in point, right now, on the product that you see there, we have external scan, cloud scan, web application scan, dark web scan, and, oh, certificate scan. We can also do internal scans, asset discovery scans, agent scans, that kind of thing. We’re looking into mobile application scans, PCI scans, etc., so there’s no limit to what other scans can be plugged in. The second aspect of that that is more of an architectural point in that with these other scan tools, let’s say a customer of ours has a different scan tool that, you know, they love, they’ve used for years, you know, etc., we can just tap into that API and pull that assessment data into what we call our ingestion engine and still pull that into our analytics platform, our cyber loss data prediction platform.
Greg: Great, Jim, thanks for that presentation. I’m just curious, the virtual CISO service that you provide, is that becoming more popular, and if so, how do you vet your virtual CISOs?
Jim: That’s a very good question. So yes, there’s no question that’s becoming more popular. My kind of tongue-in-cheek answer would be, very carefully is how I vet them right right now. We’re able to meet the demand with myself and an individual that I’ve been working with for over 10 years. This individual was acting—when I took the job at ExactTarget, I needed a kind of an outside third party to do a gap assessment on our security program to say, you know, where are the gaps for us, to be able to get ISO 27001 certified—this individual came in and did that gap assessment for us. And so that’s the other vCISO that we have available through Trava right now, along with myself.
Greg: Great, thank you again.
Jim: Thank you very much for the opportunity, it was my pleasure. If anybody wants to reach out to me, my email should be on the presentation. It’s just jim.goldman@travasecurity.com.
Audience Question: Hey, Greg. Yes, Chris, I have a question for Jim. Do you, does your organization get involved with, and if yes, how so, with the incident response? It seems to be a concern that these small and medium-sized businesses would have, without being able to parachute in some of the big players in the industry.
Jim: So we do not, and that’s sort of on purpose, because that is almost playing in the sandbox of our channel partners who are managed security service providers that have made the investment to have a 24/7, you know, security operations center open and have the incident response teams ready to go, that type of thing. So we partner, but we, that’s not something we do directly.
Audience Response: Thank you.
— End of transcript —