Last updated: Septemeber 19, 2025
Offensive cybersecurity is a crucial part of protecting your business. It’s a proactive approach of simulating cyberattacks to identify and plug vulnerabilities before threat actors can target them.
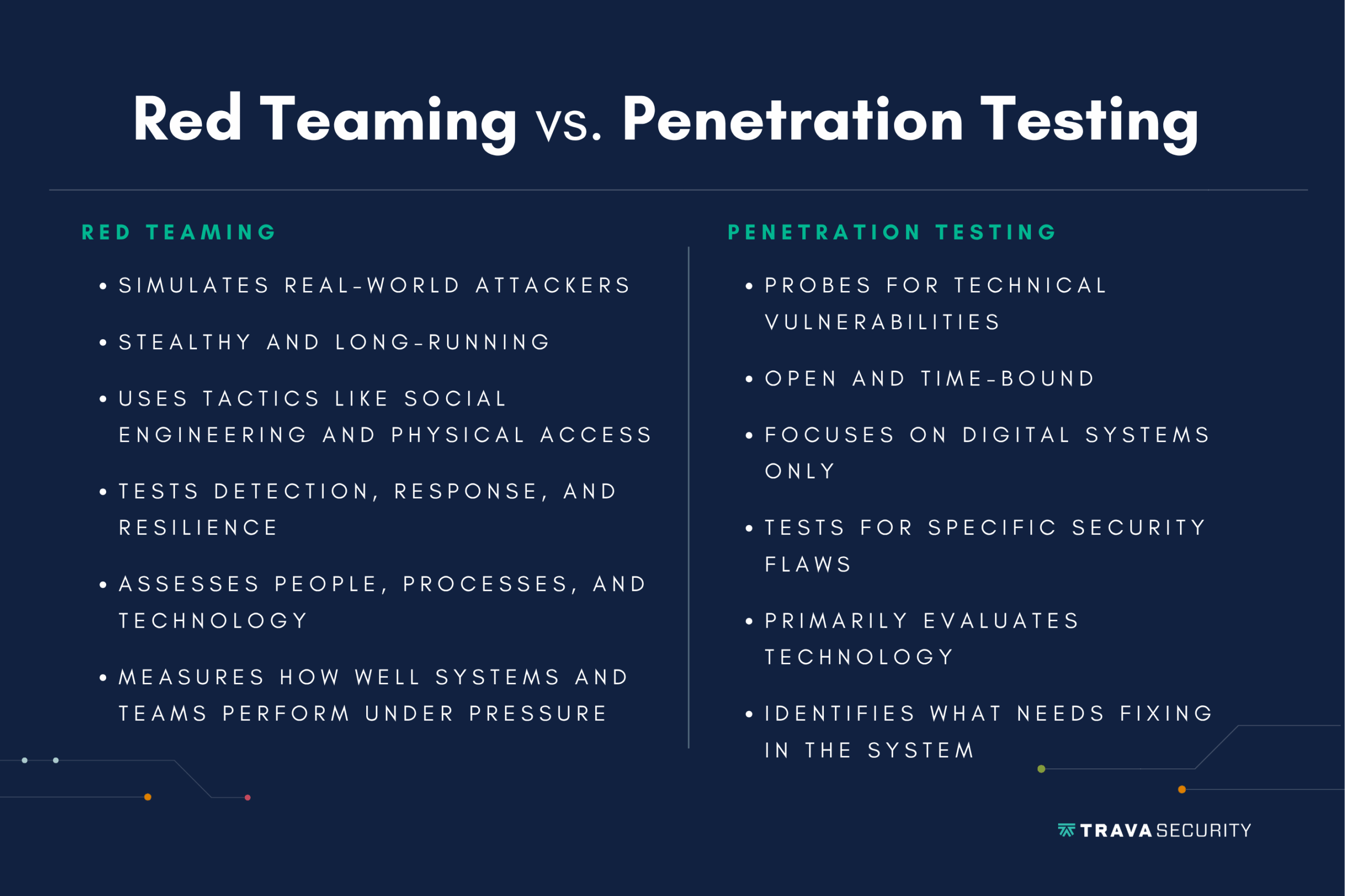
“Red team penetration testing” refers to two forms of security management: red teaming and penetration testing. While penetration testing focuses on identifying and exploiting technical weaknesses in systems or applications, red teaming goes a step further. A red team mimics real attackers by targeting not just technology but also human factors, processes, and organizational blind spots. It’s about testing your defenses as a whole, not just individual components.
This guide to red teaming vs. penetration testing highlights the business value of each security strategy. Keep reading to learn how to use them to protect your company from cybercrime.
Red Team vs. Penetration Testing: Key Differences Explained
The difference between penetration testing and red teaming comes down to their approach and scope. Here’s what you need to know about each.
What Is Penetration Testing?
Penetration testing is a focused security assessment designed to simulate how an attacker could exploit vulnerabilities in a system or app. It’s usually limited by a goal.
For example, a team may be tasked with testing your end device protection or network security. The pen test team typically won’t go beyond its scope and won’t worry about remaining stealthy while trying to breach these protected systems.
What Is Red Teaming?
Red teaming is another security assessment that simulates how attackers could exploit your protected systems. However, it’s a broader, stealthier process than penetration testing. Red teams simulate real-world threat actors.
Instead of just probing for weaknesses within a specific system, a red team may try social engineering, physical access attempts, and organizational weaknesses. The work goes beyond testing for technical exploits to also assess your ability to detect threats, respond to incidents, and remain resilient under pressure.

How Red Teaming and Penetration Testing Work Together
Most companies can benefit from penetration testing and red teaming, so don’t feel like you need to choose one or the other. You’ll learn the most by testing your defenses with both practices. Organizations often begin with penetration testing to identify and assess known vulnerabilities and risks. Think of this like testing the lock on a door to make sure that it will keep people out.
Red teaming is like a more advanced test for your company’s security. Instead of just testing the lock, you’re asking a would-be burglar to look for alternative entries, bypass your doorbell camera, and see if your guards react to their probing.
Why Red Teaming and Penetration Testing Matters
Penetration testing is an excellent tool for catching security misconfigurations and known vulnerabilities quickly. This makes it a good fit for regular scans and event-triggered reviews, such as after updating key pieces of digital infrastructure.
Red teaming tests the overall effectiveness of your controls in real-world attack scenarios. It helps identify gaps that could be exploited, which may not be revealed through traditional penetration testing.
Managed Penetration Testing and Red Teaming
You can try working your way through penetration testing internally, or outsource the job to an expert. Most companies choose outsourcing for the time and money-saving benefits it offers. Here’s a closer look.
What Managed Security Services Provide
Managed security services offer on-demand penetration testing and red teaming from cybersecurity experts. You can schedule these tests whenever you need them and stay focused on your core business while receiving personalized guidance from high-level specialists.
Managed security services also offer:
- Ongoing assessments, reporting, and support
- Dashboards for real-time security insights
- Remediation recommendations to help you fix the problems identified
- Threat intelligence-informed scenarios, which more closely replicate real-world attacks
- Help with creating clear documentation for board reports and compliance audits
Internal teams often lack the time and expertise to regularly complete these tasks without disrupting critical work. Managed service providers like Trava can step in to fill that gap while scaling with your team’s needs. This gives you access to the support you need on-demand so your core team members can stay focused on what they do best.
The Business Value of Managed Services
So, what kind of business value can you expect from managed service providers? Here are some of the most important advantages over an internal, DIY approach:
- Ongoing insight: Managed service providers offer real-time visibility into threats and weaknesses with recurring tests.
- Faster remediation: Experts working on your behalf will find and flag issues earlier so you can fix them before threat actors discover them.
- Automation and oversight: External teams have access to the latest tools and insights into emerging industry practices. They can automate manual processes to save you time and provide oversight support that accounts for emerging threats.
- Improved compliance: Regular testing can make it easier to meet important regulatory requirements. You can leverage this to pursue a new cybersecurity certification, which could become a tool for winning clients.
Finding Your Ideal Team
If you’re ready to unlock the business value of managed services, the next step is finding the right penetration testing provider or red team. Here are some tips to help:
- Look for industry experience: Focus on teams that have a background in fighting industry-specific threats. These should be better-equipped to help your company avoid its most significant risks.
- Technical and social: Teams should have experience in technical and social attack vectors. If they only have one or the other, they’re not the right fit for your testing needs.
- Custom attack scenarios: Look for providers that offer customized attack scenarios based on your infrastructure. A managed service should never use a template without adjusting it to match your unique risk profile.
- Ability to collaborate with blue team: You may want a team that can complete exercises with a blue team (which protects your company in the simulated attack). This can provide deeper insights into your cybersecurity potential.
It’ll also be important to compare multiple teams before making a hiring decision. Ask questions about your goals, budget, and timeline to zero in on the best option. You may also want to request reviews and case studies.
Does Your Company Need a Red Team or a Penetration Tester?
Red teams and penetration testing have become crucial components of modern offensive cybersecurity. It’s a proactive investment that can help you find and fix the kinds of real-world issues that a standard penetration test could miss.
Red team testing could be right for your company if:
- You’ve met your basic compliance goals and want to mature your security posture
- You’ve never tested your incident response capabilities in a live attack scenario
- Your industry is especially at risk for cybercrime
- Your leadership needs visibility into how an internal team would perform in a real attack
Penetration testing could also be a good fit for your company, especially if you recently upgraded a central system or swapped to a new platform. Trava Security can help. We offer penetration testing services that leave no stone unturned. Our comprehensive process covers everything from web apps and external networks to cloud platforms and internal apps. Work with Trava’s experts to help you tackle gaps and vulnerabilities in your system.
Red Team Penetration Testing FAQs
What Is Red Team Penetration Testing?
“Red team penetration testing” is actually a combination of two separate cybersecurity measures: red teaming and penetration testing. While penetration testing focuses on finding and exploiting technical vulnerabilities in systems or applications, red teaming takes a broader approach by simulating a full-scale, real-world attack.
Red teaming emphasizes stealth, persistence, and strategy in a way that pen tests don’t. This makes it a valuable tool for assessing your company’s real-world defensive capabilities, especially in under-tested areas like social engineering and physical access.
Why Do People Think That Red Teaming and Penetration Testing Are The Same?
Red teaming and penetration testing are often confused because they share similarities on the surface level. Both involve simulating cyberattacks to test how your organization would respond in a real-world scenario.
However, these two processes aren’t the same. Penetration tests are short-term and narrowly scoped, while red teaming is broad and strategic, leveraging stealth and multiple methods of access.
What Is the Difference Between Red Team and Blue Team Testing?
Red team and blue team testing are two sides of the same cybersecurity process. A red team simulates attackers attempting to breach an organization, while a blue team plays the role of employees in that organization trying to fend off the attack.
Your organization may benefit from using red and blue teams together. Joint tests will make each side work harder to achieve its objective. That can help you discover gaps in processes, defenses, and people that may not have come out in a one-sided test.
Why Would an Organization Hire a Red Team?
Organizations hire red teams to assess their preparedness for cyberattacks. The red team helps the company probe its defenses for weaknesses in a way that simulates how real hackers would behave. This gives the company the opportunity to find and fix gaps before they can be exploited.
What Is an Example of Red Teaming?
A red team might start by sending a round of phishing emails to your employees. These would try to trick employees into clicking on a malicious link. If an employee does so, the red team would gain access to your network and could escalate their privileges through various strategies to simulate damage.


