Published July 17, 2025
Modern businesses are more connected and more exposed than ever before. From employee laptops and smartphones to remote WiFi networks and cloud services, every digital touchpoint is a potential entryway for attackers. These may not get exploited tomorrow, but if you don’t have defenses in place, it could only be a matter of time.
That’s where attack surface management (ASM) comes in. It’s a proactive cybersecurity strategy designed to reduce these risks. Keep reading to learn how to use it to protect your business in the increasingly complex cybersecurity landscape.
What Is Attack Surface Management?
An organization’s attack surface is the sum of all potential entry points a bad actor may use to access its systems, data, or infrastructure. This includes:
- Physical devices like laptops, smartphones, and IoT-connected machines
- Software
- Networks
- Cloud infrastructure
- Mobile applications
Attack surface management is the practice of identifying these entry points and installing defenses to make them more resilient. It also includes continuous monitoring to help companies identify and respond to new risks as they arise. This makes ASM an ongoing process, rather than a one-time event.
ASM is also a key component of a broader cybersecurity strategy known as Continuous Threat Exposure Management (CTEM). CTEM is a proactive, continuous approach to evaluating and reducing risk exposure across the entire attack surface. It combines ASM with vulnerability management, threat intelligence, and risk prioritization to provide a more unified and strategic defense.
The Growth of Attack Surfaces
Attack surface management has become more important as workplaces have adopted more robust digital systems. Today’s hackers have more avenues to exploit than ever, thanks to the growth of:
- Remote work
- User-supplied devices
- Cloud-based apps and multi-cloud environments
- Digital partnerships with third-party vendors
Companies use attack surface management tools to keep these risks contained. There are several options on the market that your business may want to consider, including automated platforms, expert consulting, and bespoke services. More on these in a bit.
Key Components of Attack Surface Management Solutions
Continuous attack surface management can mean different things to different companies. But the key components are typically:
- Discovery: Automatically identifying assets that could be exploited
- Classification: Categorizing assets based on the types of risks involved, who has ownership of them, and other relevant factors
- Prioritization: Ranking assets by the amount of risk they pose so you know where to focus your defensive efforts and budget first
- Remediation: Addressing any vulnerabilities found and designing long-term solutions to reduce risk
Attack Surface Management vs Vulnerability Management
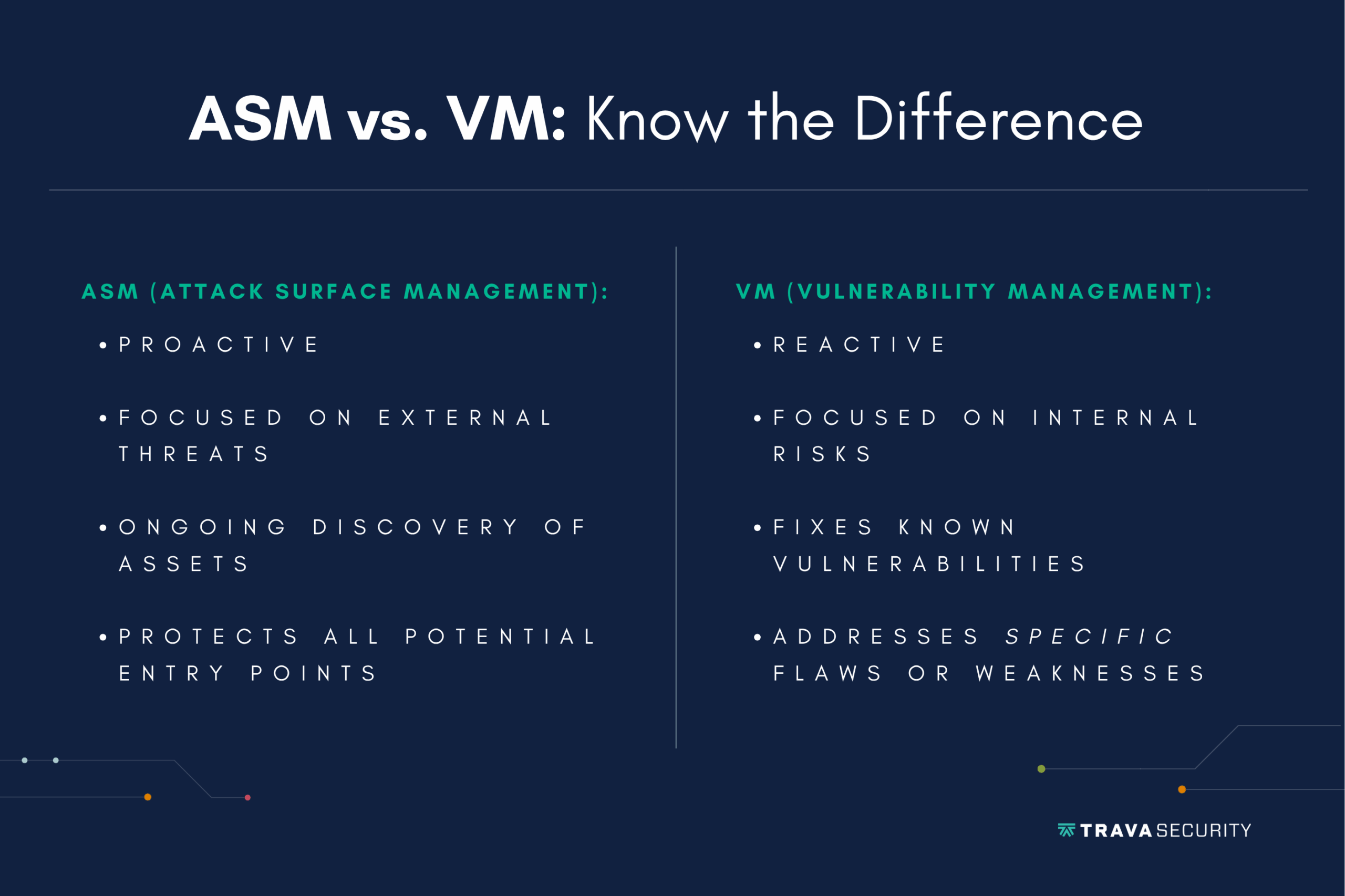
Most companies don’t have unlimited money to spend on cybersecurity. So, you may need to justify why it’s worth investing in ASM instead of an alternative service, like vulnerability management (VM). To make the case, you’ll first need to know how the two services differ.
Attack surface management is broader than vulnerability management. It focuses on protecting every entry point a hacker could use in a breach, while VM is more about addressing vulnerabilities you’ve already found.
You’ll sometimes see ASM called external attack surface management, which gets at another key difference. ASM focuses primarily on external-facing assets that someone outside of your organization could use to get into it. That could be forgotten cloud instances, public APIs, and unregistered subdomains, among other risks.
Threat vulnerability management tends to focus more on risks within the internal environment, including:
- Patching outdated software
- Scanning internal networks for unauthorized users
- Fixing misconfigurations that could be exploited
ASM and VM protect your business in different ways, which means you may want to use each. You can contact Trava for a vulnerability assessment to learn more about where your biggest risks lie.
Choosing Between Attack Surface Management Vendors
Once you’re ready to improve your attack surface risk management, the next step will be partnering with a vendor to make it happen. You can choose from a variety of tools and services, which will each protect your business in slightly different ways. Here are some key factors to consider when comparing options.
We’ve also shared some tips for mitigating risks when hiring vendors here.
Ease of Use
First, consider whether a vendor’s solution will be easy for your team to use. That means looking for features like:
- An intuitive dashboard that’s easy to navigate
- Clear reports to explain findings and share recommendations for addressing risks
- Customer service availability that meets your needs
- Easy onboarding and ongoing support to help train your team
There are too many attack surface management solutions to put up with one that makes life difficult for your employees. So, do some research, test a few options, and look up demos to find the right fit for your team.
Continuous Monitoring Services
It’s also essential to choose a solution that offers real-time monitoring. Some tools scan constantly, while others only do so on a fixed schedule, like once a week. Try to choose a platform that’s always looking for risks, if you can. This will help you find and fix vulnerabilities as they arise instead of leaving time for hackers to exploit them.
Contextual Risk Prioritization
Next, look for tools that will prioritize risks, so you know where to focus your attention first. This can help you optimize how you spend resources, so you’re always addressing the most significant risks to your business first. It can help you get more value out of an ASM service than what you’d get without risk prioritization support.
Integration With Existing Tools
Another critical factor is finding a solution that integrates well with your existing tools. If an ASM platform is incompatible with part of your existing digital landscape, that app, database, or network may be left unprotected.
Pricing Transparency and Scalability
Finally, prioritize vendors that offer pricing transparency and easy scalability. You want to know exactly how much you’re paying for ASM support and how that could change if your needs expand or contract over time.
If you’re searching for a vendor that offers each of these benefits, look no further than Trava. Our cyber attack surface management solutions provide powerful protection in personalized packages that are easy to scale.
The Growing Importance of Attack Surface Management
Continuous attack surface management is only becoming more important as technology improves. Finding the right solution for your business will keep it protected as the way we work continues to evolve.
When you’re ready to start, Trava has you covered with bespoke ASM solutions to minimize your attack surface and set the stage for growth. So, why wait to get help with comprehensive cybersecurity management?
Frequently Asked Questions (FAQ)
1. What is attack surface management in cybersecurity?
Attack surface management (ASM) is a cybersecurity process that continuously identifies, monitors, and secures all potential entry points that hackers could exploit—such as devices, apps, and cloud assets. It helps reduce cyber risk before threats occur.
2. Why is attack surface management important for businesses?
Businesses today rely on cloud apps, remote work, and third-party tools, which expand their digital footprint. ASM helps identify hidden risks, prevent data breaches, and protect external-facing assets that traditional tools may miss.
3. What are examples of an attack surface?
Common attack surface examples include exposed APIs, cloud misconfigurations, forgotten subdomains, employee laptops, mobile apps, and third-party integrations. Anything connected to the internet can be part of your attack surface.
4. How does attack surface management work?
ASM works by continuously discovering digital assets, classifying them by risk, prioritizing vulnerabilities, and enabling remediation. Many businesses use automated ASM platforms for real-time monitoring and threat detection.
5. What’s the difference between ASM and vulnerability management?
ASM focuses on identifying and securing all possible attack entry points—especially external-facing ones—while vulnerability management addresses known internal issues like unpatched software or misconfigurations. They are complementary strategies.


